BreakICT 2022 CTF Walkthrough (Part 1)
The following challenges are from the BreakICT CTF for OzSec 2022, an annual cybersecurity conference in Wichita, KS. Here in part 1 we will take on four different challenges from the CTF.
Epic Server Beta! (v.2)
Challenge Description
A developer known as the "Breadministrator" has just created a new site hosted in GCP. It utilizes App engine to host static pages for now.
https://alpha-test-dot-breakict.uc.r.appspot.com/
Rumor has it that the Breadministrator accidentally published some data in the very first revision of the app. The app was shortly updated afterwards. Users a part of the private beta claimed the app was up with the secret information on February 25th, 2022, at approximately 17:22, the app was deployed from CST
Can you find any proof or content from the initial private beta?
Note: regions did not change throughout deployments
P.S.: You don't need to run directory scans, but may need to mangle/transform the URL to find the exact time (down to seconds) of when the app was first deployed.
https://alpha-test-dot-breakict.uc.r.appspot.com/
Challenge Walkthrough
Visiting the site we see that it now has redacted some private information.
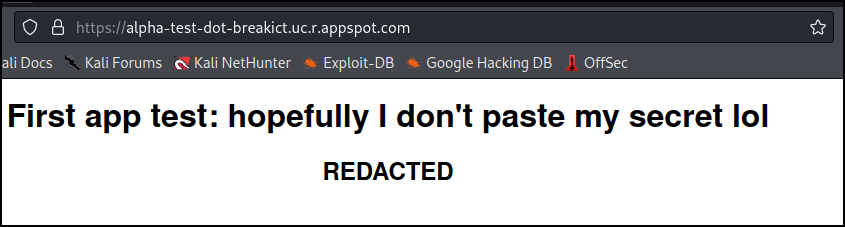
Searching for appspot and previous versions I ran across a StackOverflow post talking about how Google Cloud doesn’t remove previous versions automatically, and all versions of an app that are published are by default still accessible via a different subdomain.
https://stackoverflow.com/questions/43430383/gcloud-app-deploy-does-not-remove-previous-versions
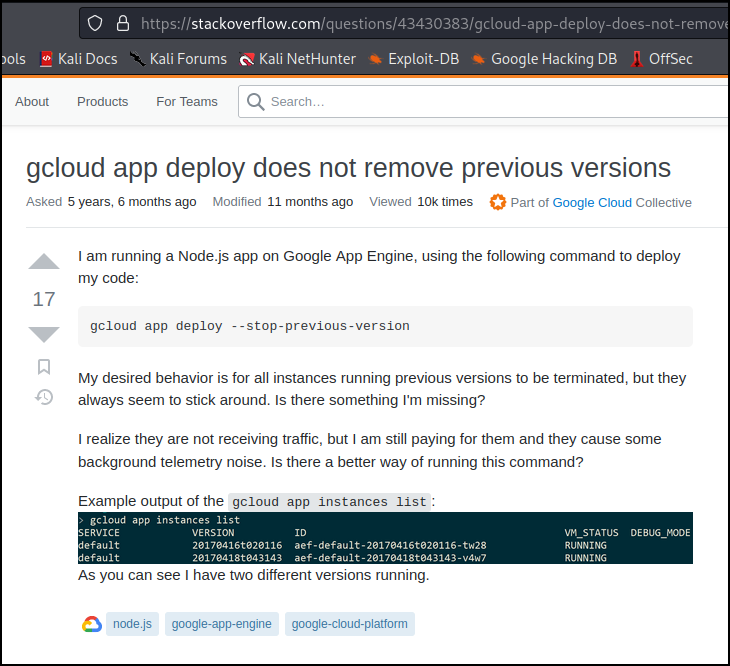
In the screenshot of the post you can see the versions are a date and time stamp: <yyyymmdd>t<hhmmss>.
Searching documentation for Google Cloud we find an example of accessing versions using a specific URL of https://<VERSION>-dot-<SERVICE>-dot-<PROJECT_ID>.<REGION_ID>.r.appspot.com
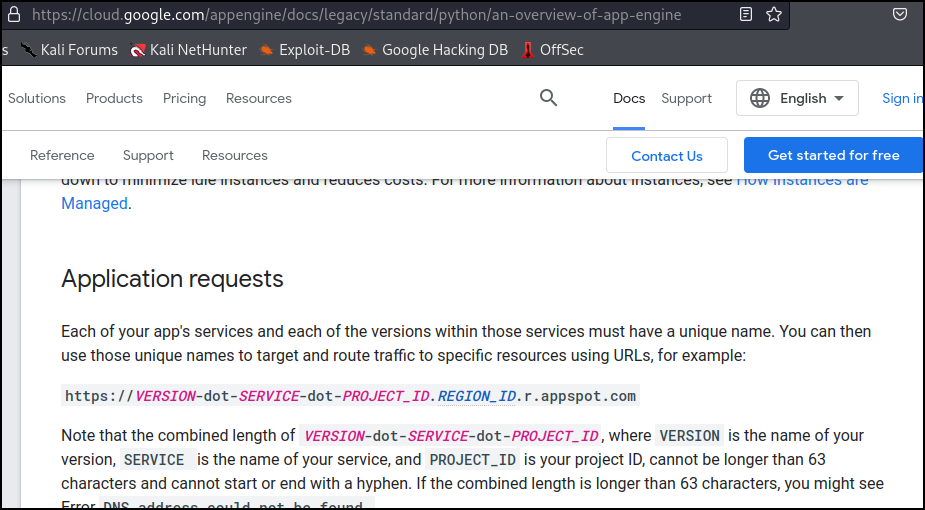
With this information, and the date and time mentioned in the challenge question, I need to find the previous version that was published sometime on February 25th, 2022, at approximately 17:22. The URL of https://20220225t1722??-dot-alpha-test-dot-breakict.uc.r.appspot.com We just need to guess the right seconds.
My approach was to use PowerShell to generate a list of URL’s and wget each of them. I would then compare the file sizes to identify any outliers.
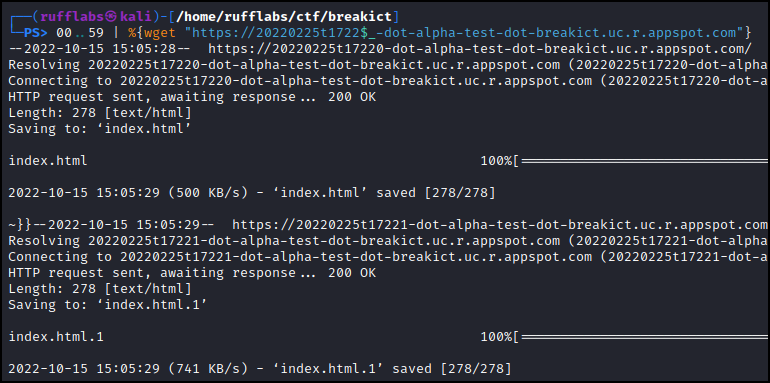
100..59 | %{wget "https://20220225t1722$_-dot-alpha-test-dot-breakict.uc.r.appspot.com"}
This downloaded one index.html for each second. Looking through the list at their file sizes I saw the one toward the end has a different file size. It is 316 bytes when all other pages are 278 bytes.
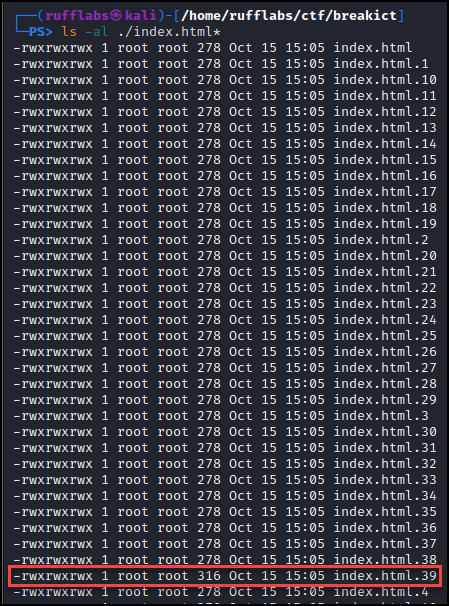
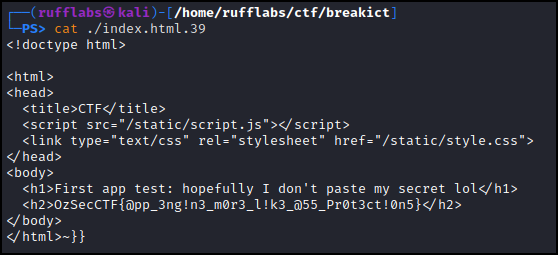
Looking at the contents of index.html.39 revealed the flag!
- Points: 350
- Flag:
OzSecCTF{@pp_3ng!n3_m0r3_l!k3_@55_Pr0t3ct!0n5}
Where the hell did I leave my bucket
Challenge Description
We believe breakict may have some type of cloud bucket blob big data lake thingy. We're looking for a secret flag.txt file. Could you find it for us pls? We don't know anything new about this organization. The bucket could be named anything
P.S.: once you've found the bucket, again, there's a flag.txt with the secret
Challenge Walkthrough
We need to find a storage account, our options are potentially AWS S3, GCP, or Azure. I will start by looking for an S3 bucket, typically companies use their company name for a bucket name so I will first just guess at breakict.s3.amazonaws.com
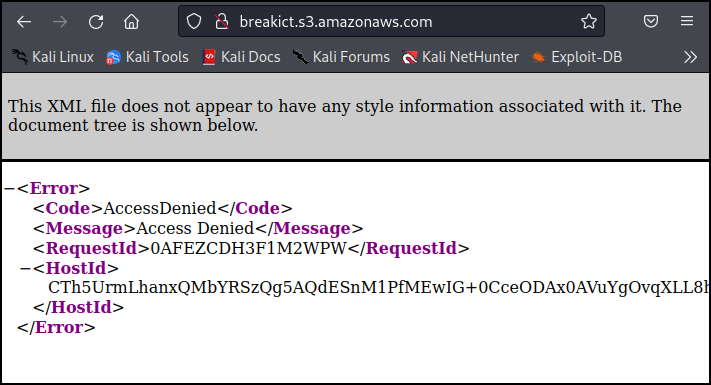
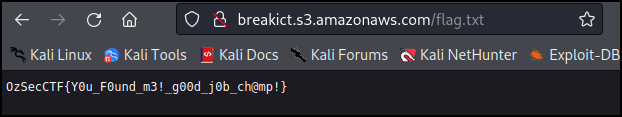
We have an access denied, this means the bucket exists, otherwise we would get a bucket does not exist error. Let’s try to grab the /flag.txt mentioned in the introduction.
- Points: 100
- Flag:
OzSecCTF{Y0u_F0und_m3!_g00d_j0b_ch@mp!}
Took my b64 and we flew it into orbit
Challenge Description
sigh here's some string we found. Decode it or somethin =0nel9Fdp91MrRTbfxGbnk0Xl5WIm9Ve0sGM7ZEVDNWZTp3T
Challenge Walkthrough
The = is a giveaway that this is most likely Base64 encoded, and since it's the first character the string is likely reversed.
Let’s throw it into CyberChef and use a recipe of Reverse, From Base64.
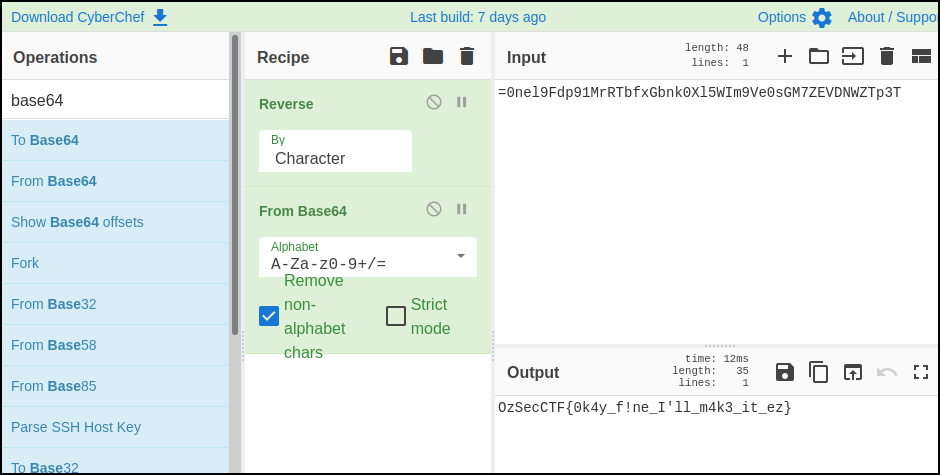
- Points: 100
- Flag:
OzSecCTF{0k4y_f!ne_I'll_m4k3_it_ez}
Cracking Kraken
Challenge Description
We’ve obtained a hashed password! We don't know what algorithm they’re hashed in, nor do we care, that's your job. Have fun! The flag is the recovered password inside of the OzSecCTF{} wrapper PS: I’ll save you the effort, the password isn’t in rockyou.txt, it’s 2022 ;)
Some details about the org the hash is from:
- The org name is BreakICT
- The org previously had a breached password, so we assume this one has been 'updated'
- The org requires at least 1 captial letter, 1 number, 1 special char, and at least 8 chars in password length
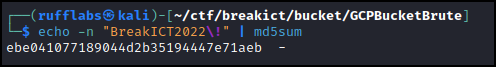
Here's the hash: ebe041077189044d2b35194447e71aeb
Challenge Walkthrough
For this one I just took a stab and guessed correctly the first try: BreakICT2022!
Running this through md5sum matches the hash provided.
- Points: 200
- Flag:
OzSecCTF{BreakICT2022!}