BreakICT 2022 CTF Walkthrough (Part 2)
The following challenges were from the BreakICT CTF for OzSec 2022, an annual cybersecurity conference in Wichita, KS. This is the final part of my two part series covering the challenges from this CTF.
Ping me if we get hacced
Challenge Description
I've got a pcap of a machine that was hacced. After some review, our next gen firewall says the traffic is clean. But that's a lie, could you take a look and see maybe what data was exfiltrated?
Challenge Walkthrough
Opened the packet capture up in Wireshark.
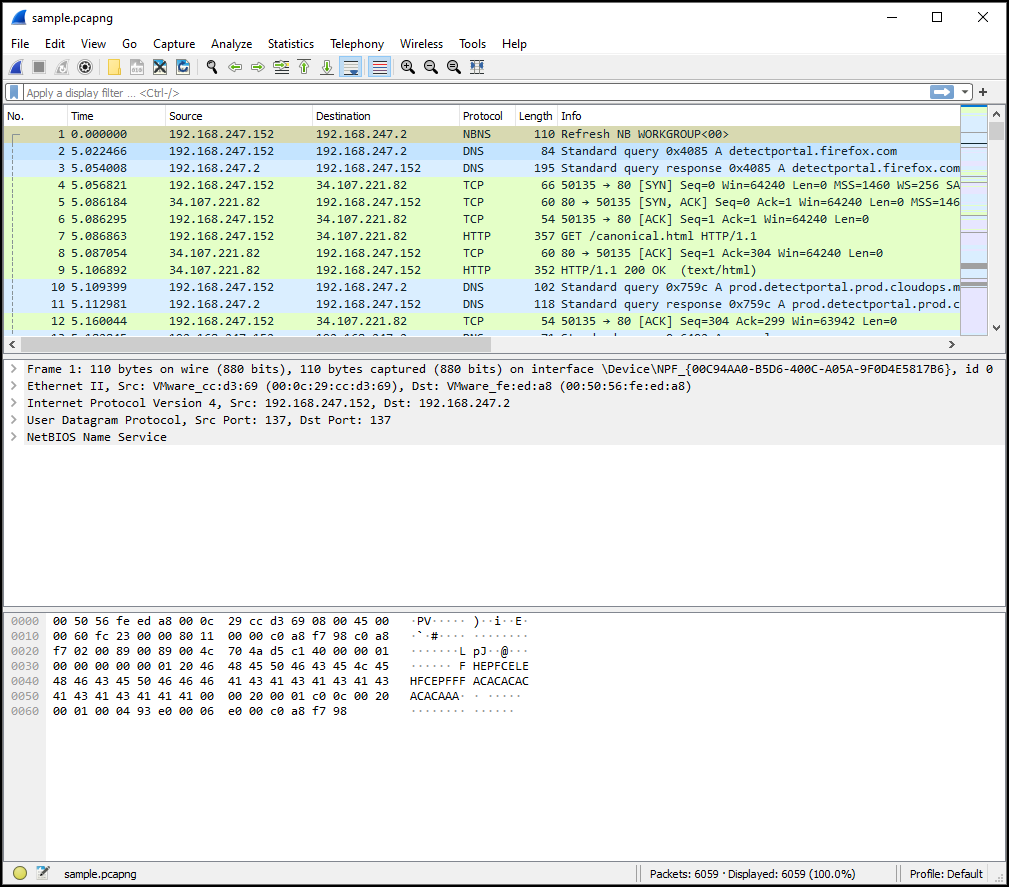
Since the title of this challenge is “Ping me” I filtered on icmp packets.
We can see a whoami command in the first ping packet.
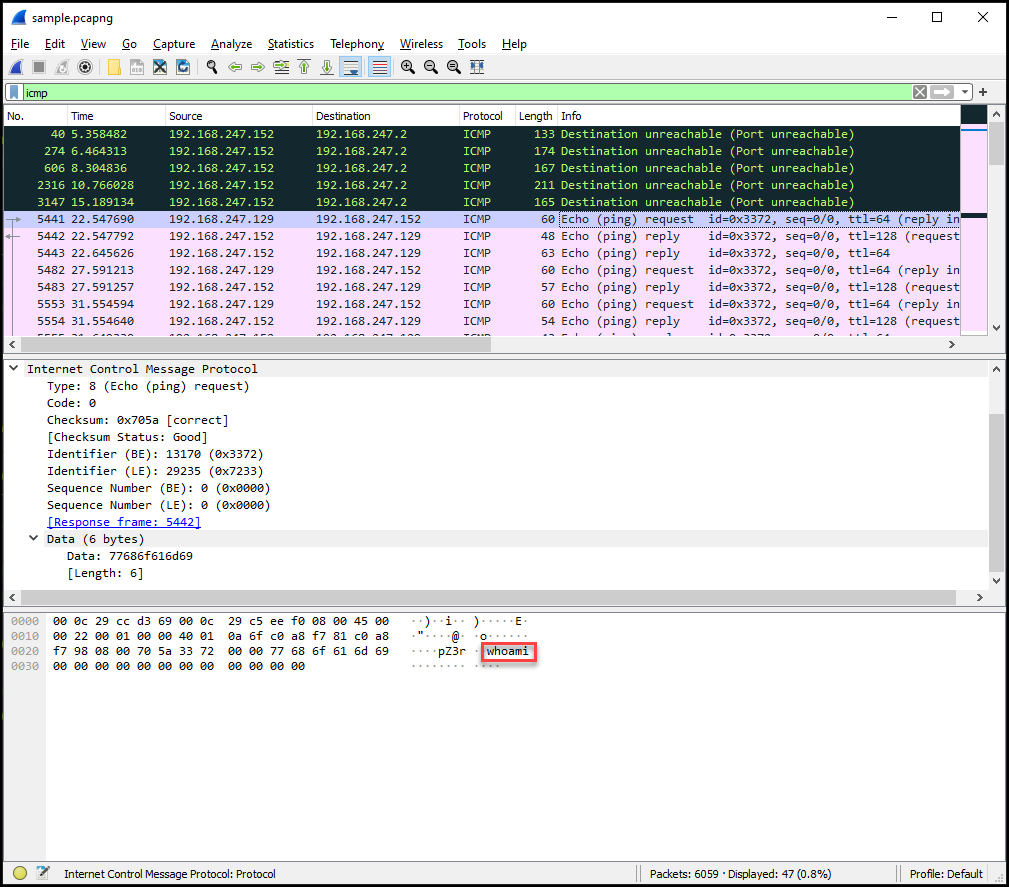
Checking further in the chain, we notice an ls command..
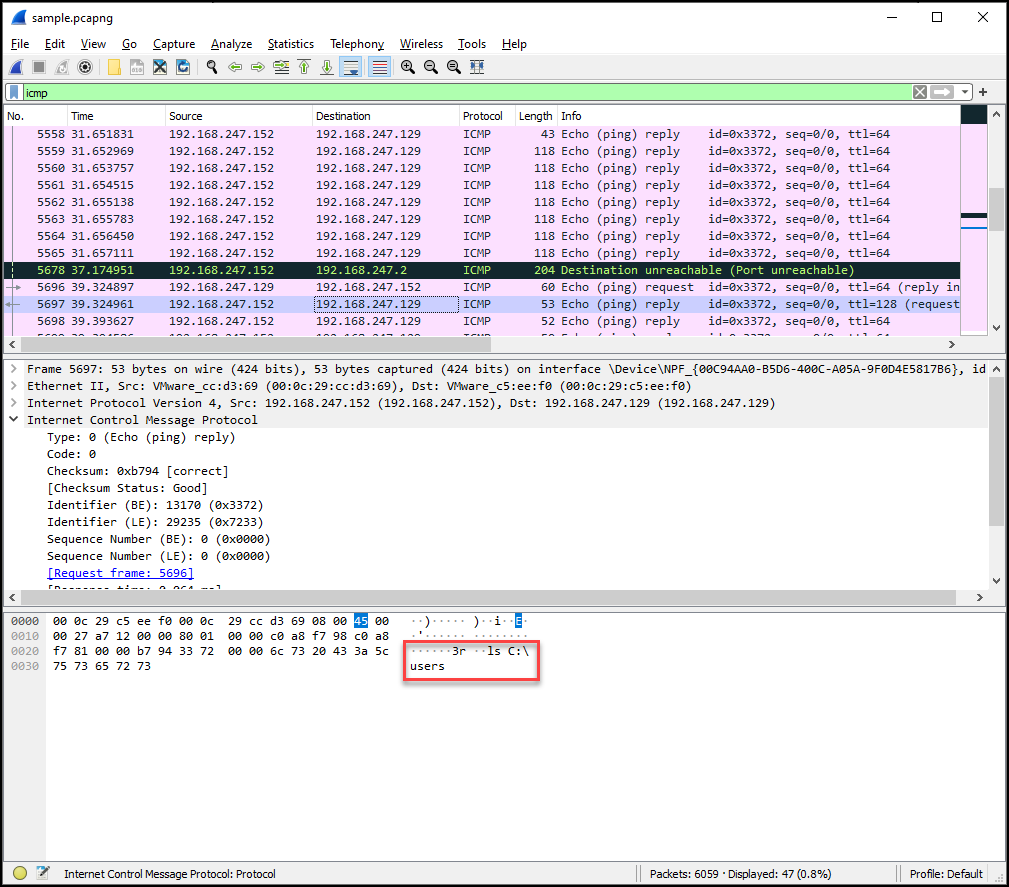
A cat...
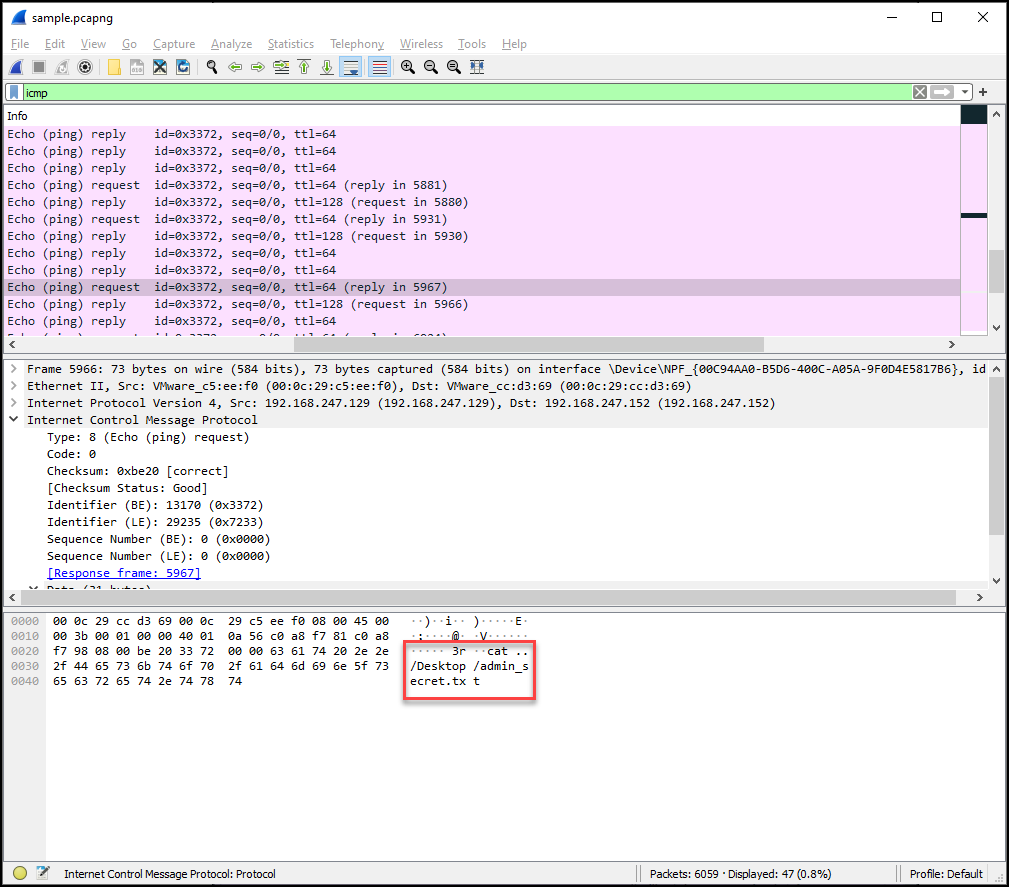
And finally the flag itself!

- Points: 100
- Flag:
OzSecCTF{M1_G@r@nd_g0_P!ng}
Do Not Start early pls
Challenge Description
There's a weird domain that showed up on our radar. Could you take a look and see if there's any information more than what we have?
1bruhwhatlmaougothacced.breakict.org
Challenge Walkthrough
Checking DNS on this domain I found a txt record that included the flag.
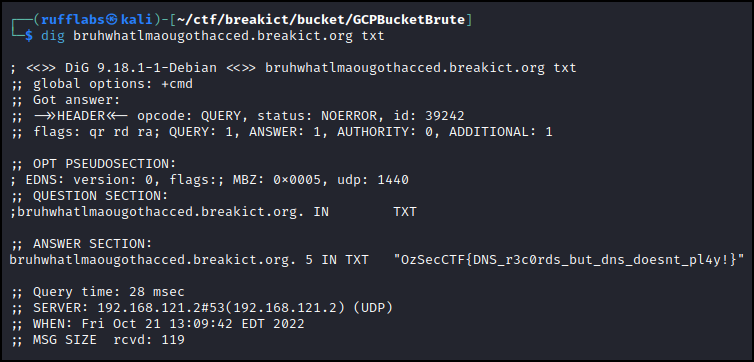
- Points: 100
- Flag:
OzSecCTF{DNS_r3c0rds_but_dns_doesnt_pl4y!}
Coffee and Carding
Challenge Description
One of our sting operations experts retrieved this image from a known cyber criminal. Can you figure out the name of the location the person was at?
FLAG will be OzSecCTF{location_name} - 5 ATTEMPTS
The location name will have no spaces, and is case insensitive

Challenge Walkthrough
00:13:37:a9:57:17 appears to be a MAC address, and this looks like a wifi pineapple.
I visited wigle.net, entered the MAC into the BSSID field and zoomed out. I saw a single entry.
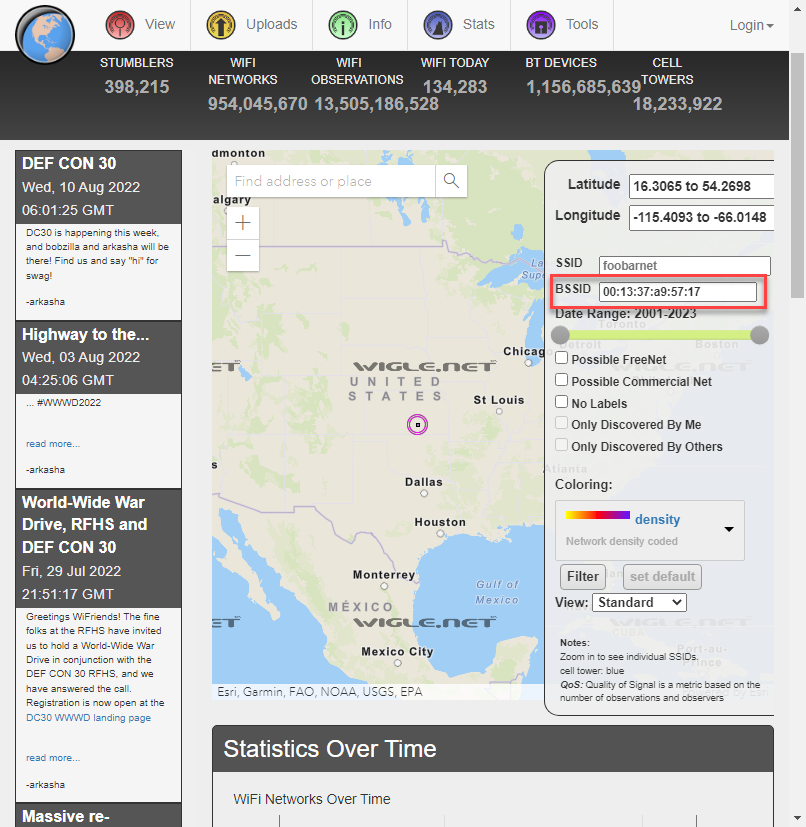
Zooming in we get a location.
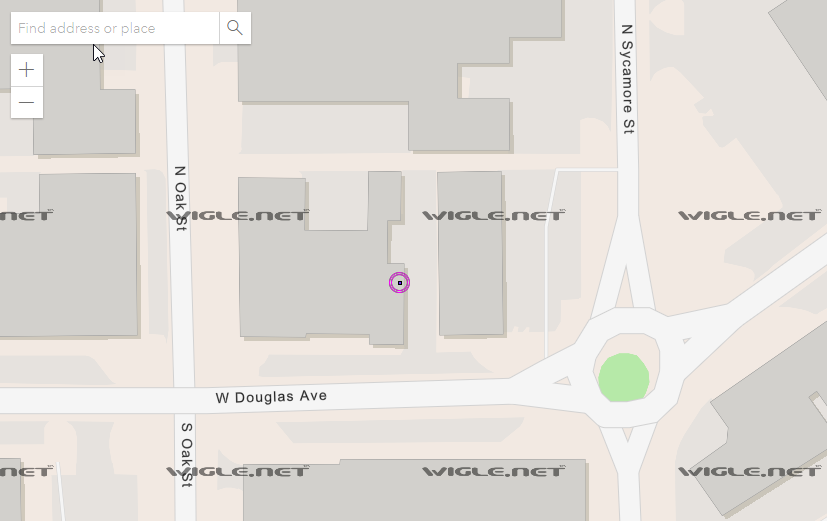
Matching up this location in Google Maps I found the cafe.
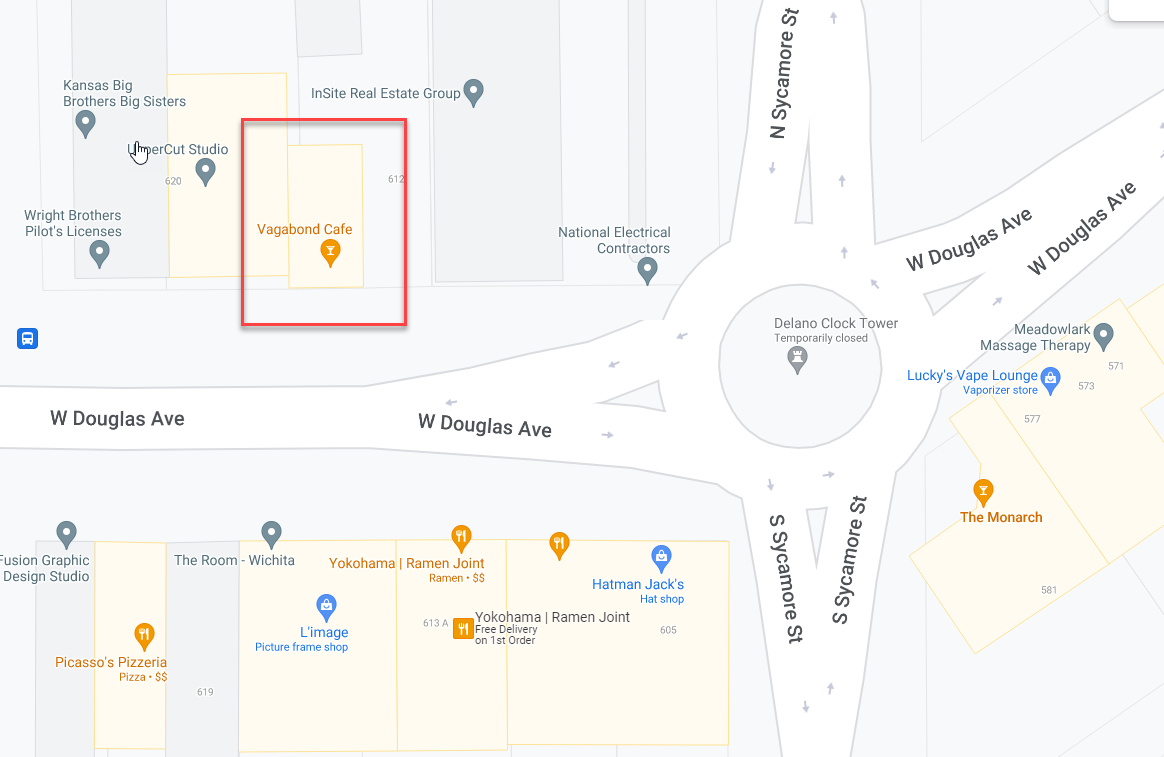
- Points: 199
- Flag:
OzSecCTF{VagabondCafe}
Classic web, Just Sayin'
Challenge Description
Web is funni bc I could literally give you the flag + solve method and you'd still run dirb on the target, wouldn't you? ;)
https://password-vault-dot-breakict.uc.r.appspot.com/
Challenge Walkthrough
Loading up the page I see a form input requesting a password, looks like it will reveal the flag if we enter the correct password.
Tried entering 'asdf' as a test. That's not it..
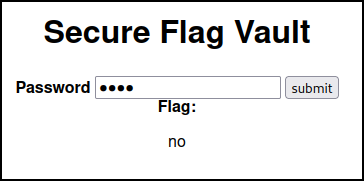
Checking source there is a script.js that is loaded. Checking this file we see a password check. The password it's checking against is right here in cleartext.
Using the above found password works, as expected.
- Points: 50
- Flag:
OzSecCTF{cl!3nt_s!d3_dw3ebS!}
I got 2 bits
Challenge Description
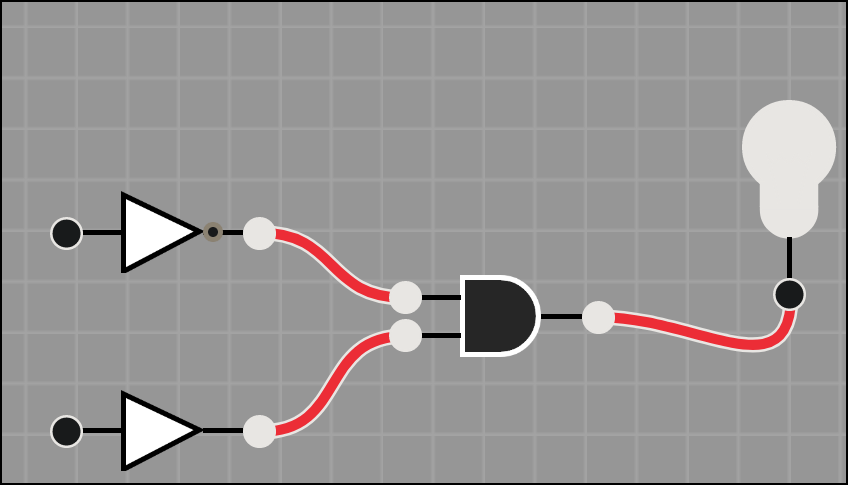
Presented to you is a logic diagram, figure out what bits will make the light bulb light up. Careful! you've got 3 attempts
IE, if your answer is (top to bottom) 1010 your flag would be OzSecCTF{1010}
Challenge Walkthrough
I had to check the hint on this one, which led to http://www.ee.surrey.ac.uk/Projects/CAL/digital-logic/gatesfunc/index.html where I found a handy chart:
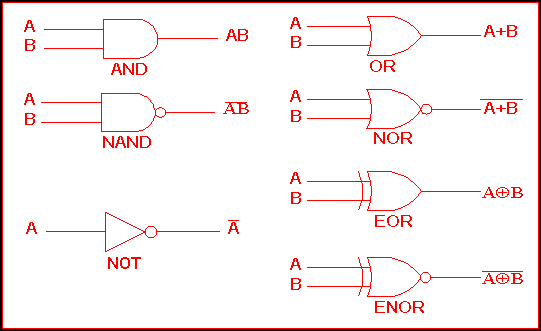
Given that, we have a NOT gateway up top, an AND gate in the middle, and I didn’t see a normal triangle so I will assume it’s the opposite of a NOT gate since it looks the same without the circle symbol.
To generate a 1 on the output of the AND gate and turn the light on we need to feed in a 0 up top which gets turned to a 1, and a 1 on the bottom.
This feeds 1, 1 into the AND gate. 1 and 1 is a 1, which turns on the light.
- Points: 100
- Flag:
OzSecCTF{01}
I got 4 bits
Challenge Description
now with 4 bits!
flag will be in format of inputs needed top to bottom, formatted left to right.
ie, if you need top to bottom 1010, the flag is OzSecCTF{1010}
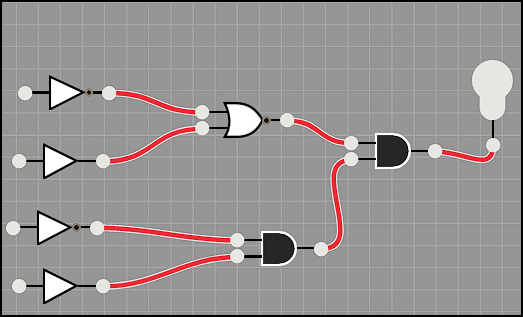
Challenge Walkthrough
This is basically the same as above, with some more complexity thrown in.
We have:
| NOT | NOR | AND |
|---|---|---|
| NORMAL | ||
| NOT | AND | |
| NORMAL |
To generate a 1 on the output side of the final AND gate, our inputs end up being:
1, 0 through the NOT and NORMAL into the NOR gate outputs a 1.
0, 1 through the NOT and NORMAL into the AND gate outputs a 1
These two 1’s go into the final AND gate and turn the light on with an output of 1.
- Points: 106
- Flag:
OzSecCTF{1001}
You get the GISt of it
Challenge Description
How much property tax was paid for the Drury plaza hotel in 2021? (special tax + general tax), decimal should be included. Flag is OzSecCTF{amount_no_special_chars_except_for_pennies}
Challenge Walkthrough
For reference, the Drury Plaza is located in Wichita, KS. The location of this local CTF.
Searching for Sedgwick County Property Tax leads to this state site:
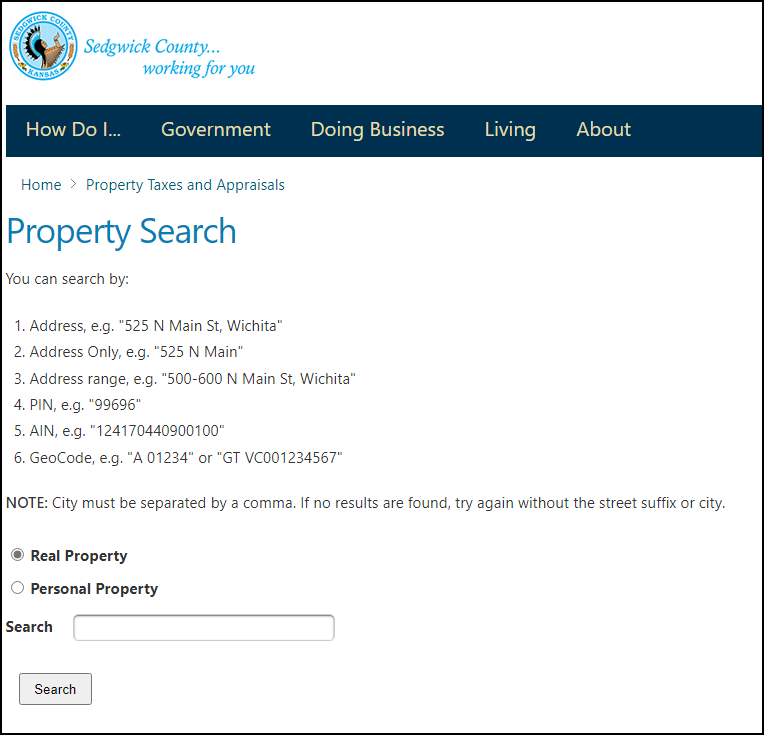
Entering the address of the hotel:
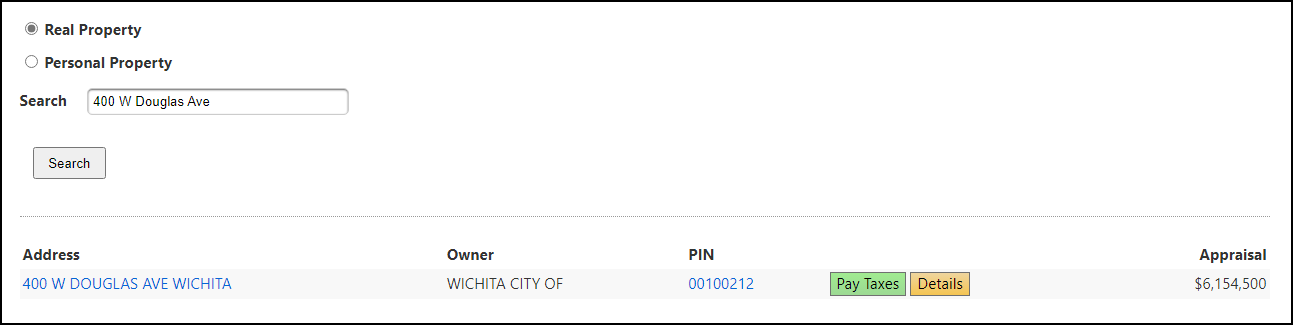
Clicking on the property link leads to the properties page. From there a transactions tab shows payments.
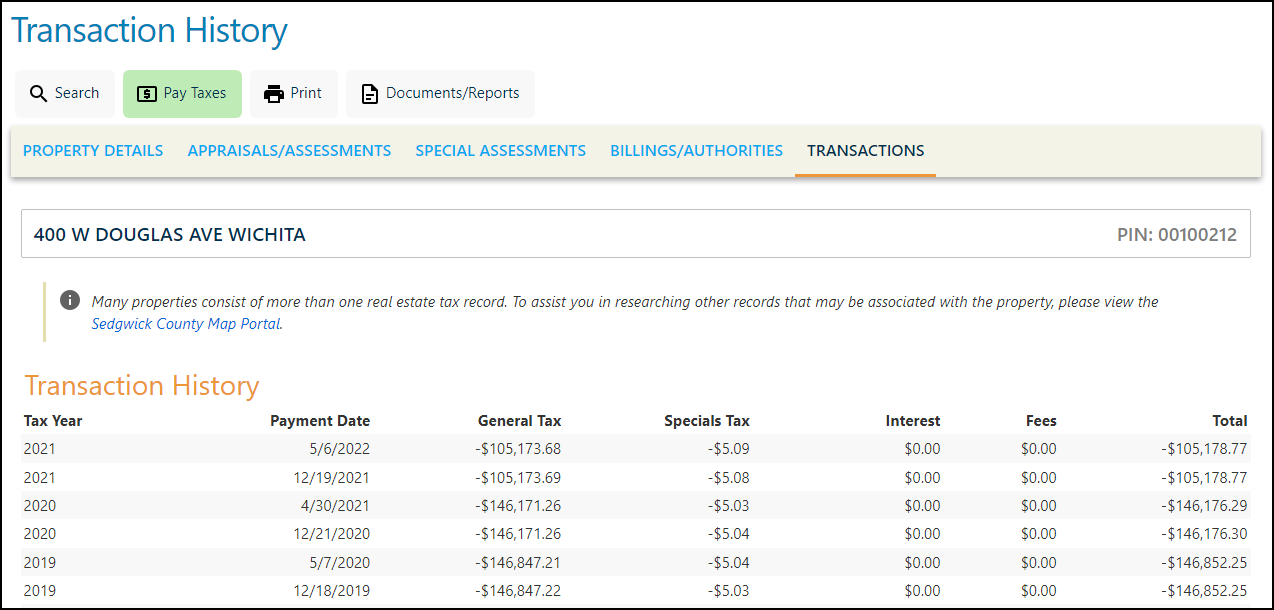
Adding up the General and Specials taxes for the two 2021 transactions gives us our flag.
- Points: 150
- Flag:
OzSecCTF{210357.54}
ASk Me anything!
Challenge Description
Below is a line of ASM code. what is the resulting value stored in EAX after the lines have all run? (INTEL SYNTAX BEST SYNTAX) Flag is OzSecCTF{your_answer} - 3 ATTEMPTS
1mov eax, 0
2inc eax
3mov ebx, 0
4inc ebx
5inc ebx
6imul eax, ebx
7xor eax, eax
Challenge Walkthrough
I don’t know assembly, but the final instruction is xor’ing eax by itself. I believe this should be 0, and that was correct:
- Points: 15
- Flag:
OzSecCTF{0}
Sanity check
Challenge Description
Sanity check!
submit this flag! OzSecCTF{4moguS}
p.s: do NOT ask for a hint on this challenge, you will regret it
Challenge Walkthrough
Kind of self explanatory…
- Points: 15
- Flag:
OzSecCTF{4moguS}
Oh CRap
Challenge Description
A client sent us over a secret to access the application we’re testing for them, but they never learn! they sent it as an image :(
If only there was some technology to convert characters from an image into a recognizable text based format.
hint for this, and future CTF's everywhere. Look at capitalized characters in the title.

Challenge Walkthrough
We have what appears to be a Base64 encoded string within an image. We need to get this into text so that we can base64 decode it.
I don't have a screenshot of this step, but I used tesseract-ocr to grab text from the image.
Pasting the results directly into CyberChef to decode we find that some characters don’t quite look right. Possibly some of the OCR was incorrect.
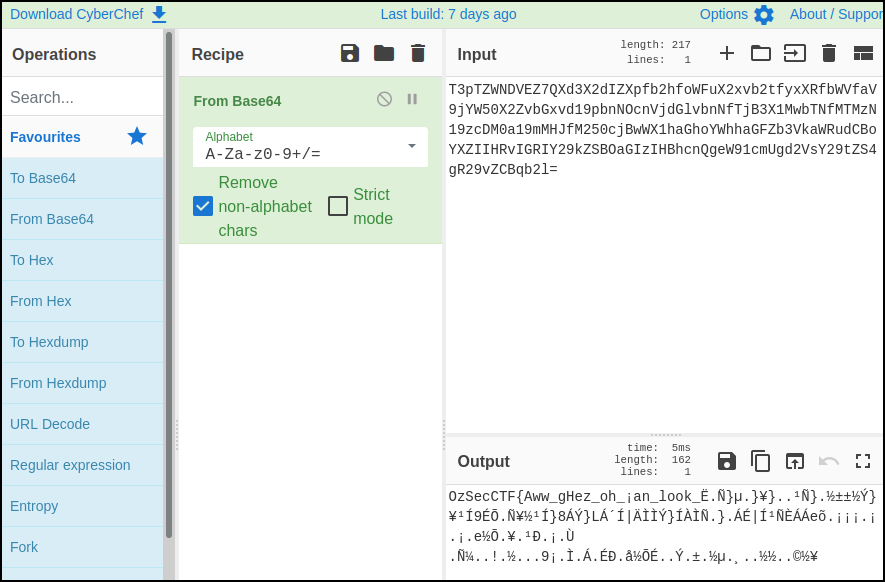
Quickly comparing the image to the text output reveals a few incorrect transcriptions.
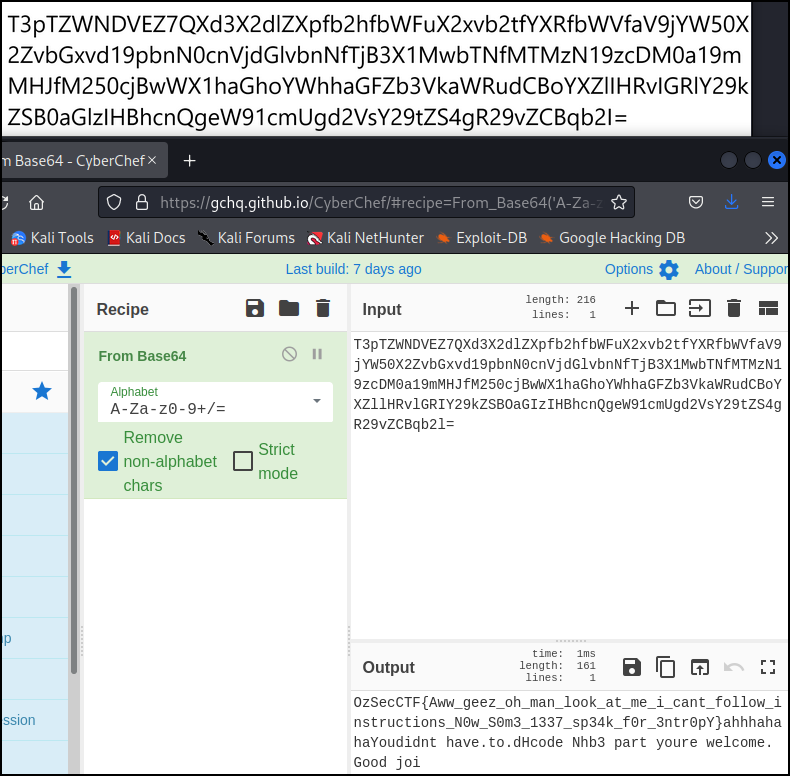
Correcting the incorrect L’s, I’s, and 0’s, we get the flag.
- Points: 150
- Flag:
OzSecCTF{Aww_geez_oh_man_look_at_me_i_cant_follow_instructions_N0w_S0m3_1337_sp34k_f0r_3ntr0pY}
Unsolved During CTF
The following challenges were not solved by me during the CTF.
cybercrime operations (NOW ON DISCORD!)
Challenge Description
We've got sting operators infiltrating every edgy online chat room we could find. This one presents promise as to holding some secret keys. Can you figure out what secret key is being kept?
Challenge Walkthrough
Visit the linked Discord server and see that an admin of the server added a bot. This bot has a secret, but will only give it to you if you are a member of an ‘ADMIN’ role.
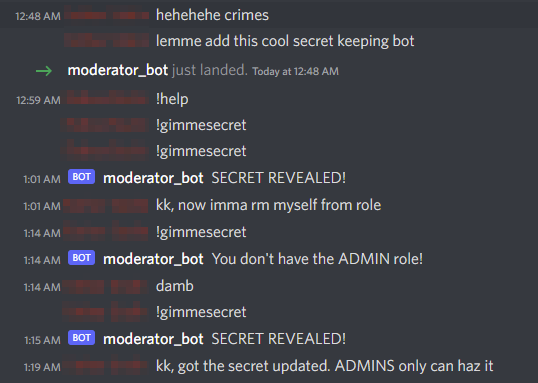
Enable Developer mode in Discord User Settings > Advanced.
Copy the ID of the bot by right clicking on it and selecting Copy ID.
The ID was: 1030181821788454982
Searching for adding a bot to a Discord server, we can see an example of the invite link. The client_id parameter is the Bot’s ID. Create a link using the ID copied.
Enter this into a browser and login to Discord and you will be presented with this dialog to add the bot to a server you are an admin on.
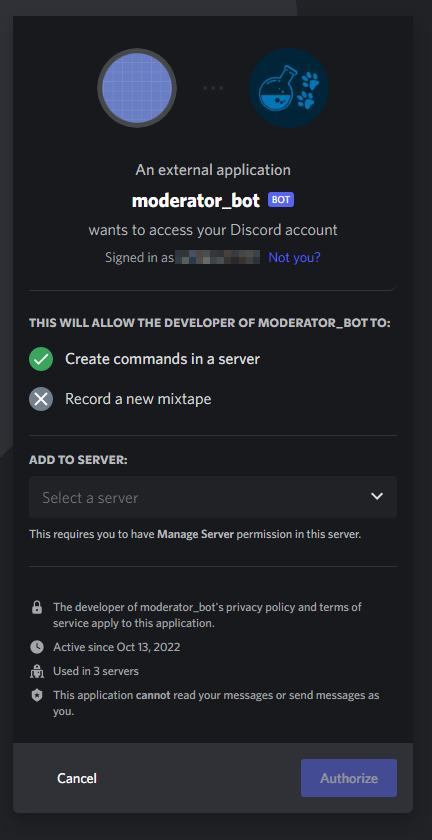
Select an appropriate server, give yourself an ADMIN role and ask for the secret!
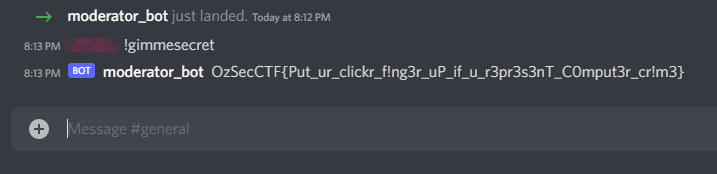
- Points: 200
- Flag:
OzSecCTF{Put_ur_clickr_f!ng3r_uP_if_u_r3pr3s3nT_C0mput3r_cr!m3}
L337H4X0R
Challenge Description
We’ve obtained a plain text message and it’s corresponding ciphertext after observing communications between threat actors, supposedly they use some type of XOR algorithm to encrypt the messages, can you crack the key?
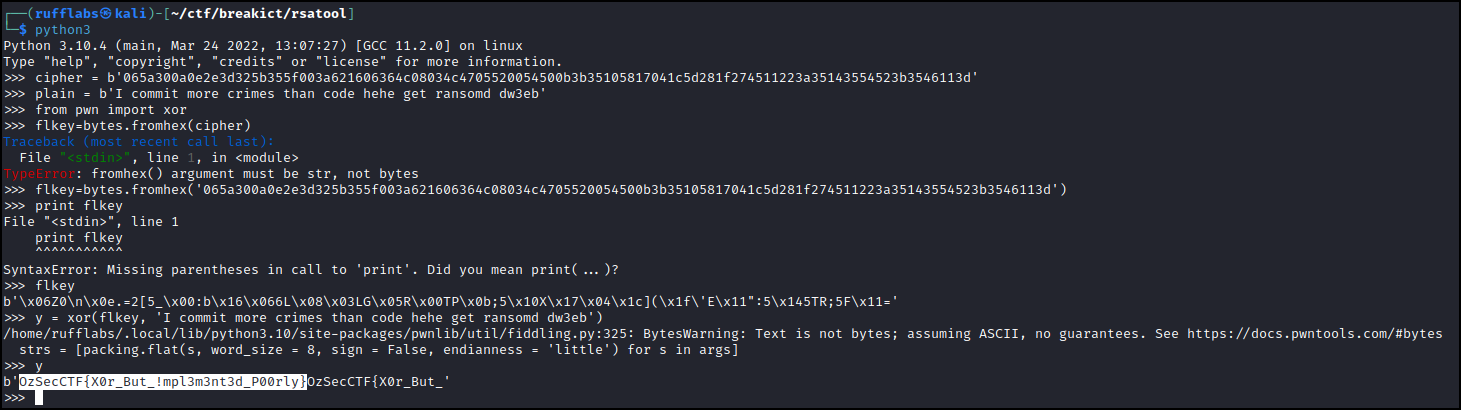
I commit more crimes than code hehe get ransomd dw3eb → 065a300a0e2e3d325b355f003a621606364c08034c4705520054500b3b35105817041c5d281f274511223a35143554523b3546113d
Challenge Walkthrough
Took quite a bit of googling, but I solved it with the help of this stackoverflow post: python - Guessing XOR secret key knowing some part of it - Stack Overflow
- Points: 125
- Flag:
OzSecCTF{X0r_But_!mpl3m3nt3d_P00rly}
Really Sorry About this
Challenge Description
We've identified an RSA public key, can you crack the private key by doing math?
'pub': (e=17, n=926137)
FLAG FORMAT WILL BE OzSecCTF{someint} , where someint is the private key.
Challenge Walkthrough
I definitely had to use the hint on this one, as this was my first exposure to an RSA crypto CTF challenge.
The hint led to http://mathonline.wikidot.com/rsa-encryption
This has the step-by-step instructions for calculating the missing private key from the known e and n values.

We can basically follow along!
Step 1
e = 17 and n = 926137
Step 2
I used factordb.com by pasting in n.
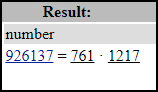
p = 761 and q = 1217
Step 3
WolframAlpha to the rescue! I learned that this symbol is phi.
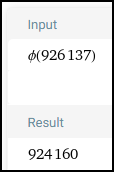
phi = 924160
Step 4
17d <weird equals> 1 (mod 924160)
Back to WolframAlpha
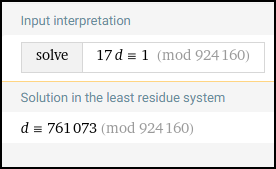
There’s the flag value.
- Points: 125
- Flag:
OzSecCTF{761073}
Too Late, Sorry!
Challenge Description
The CEO's machine got popped! We're dealing with the recovery process right now, but all we have to give you for information is this pcap. Can you figure out what c2 framework was utilized to hold a shell on this box? FLAG IS OzSecCTF{c2_name}
flag is case INSENSITIVE, 4 ATTEMPTS
free hint: https://www.thec2matrix.com/
Challenge Walkthrough
Packet capture has TLS traffic on non-standard ports.
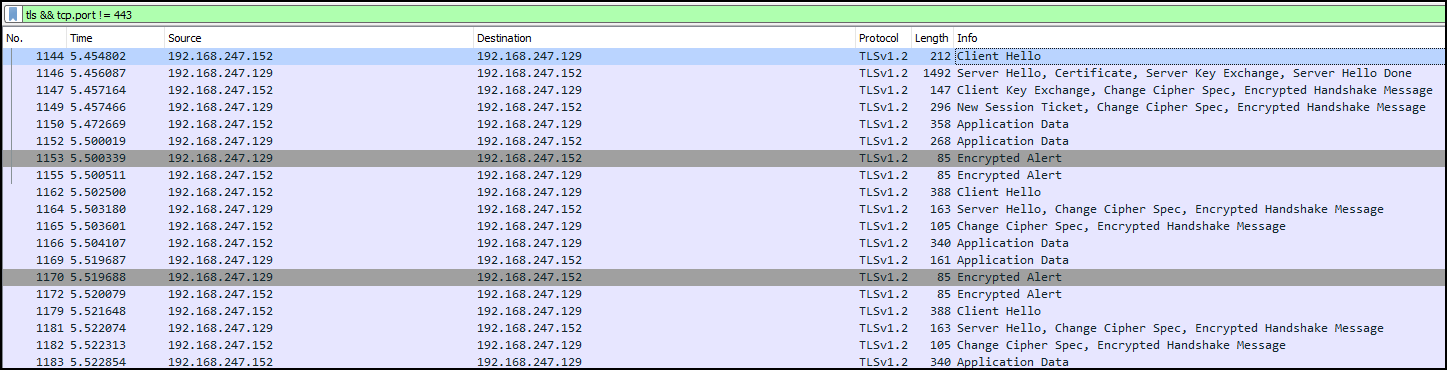
Running ja3 against the pcap we the hashes for the fingerprints of the tls traffic.
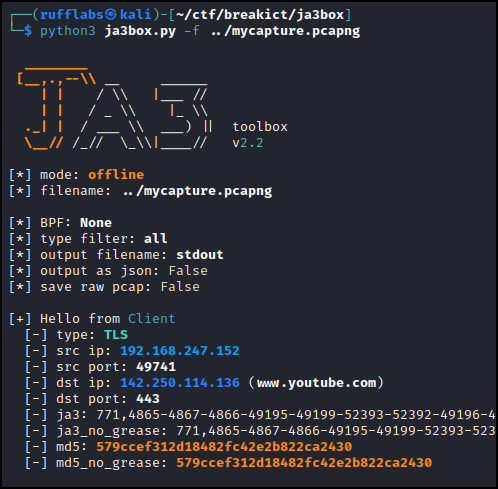
Find the traffic on non-standard ports.

Search for that hash, found the following article:
Creating Context for Better Hunting - NetWitness Community - 606384
Mentioned hash ec74a5c51106f0419184d0dd08fb05bc is for Metasploit on Kali.
- Points: 200
- Flag:
OzSecCTF{Metasploit}
Super Slow! radio
Challenge Description
I started my own pirate radio station! If you missed my first broadcast, here's a recording!
Challenge Walkthrough
An audio file encoded as a Slow-Scan TV file. SSTV is a method of displaying images over radio waves typically used in ameture radio.
Running sstv against the file results in the still image, with flag.
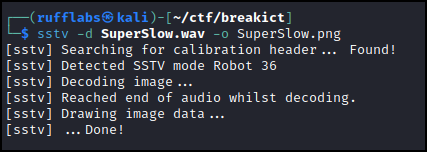

- Points: 100
- Flag:
OzSecCTF{4_My_n!x_b00m3rS_0nly!}
classic reversing
Challenge Description
heres a binary, reverse it!
Challenge Walkthrough
Checking the binary in Ghidra, I found a print_flag statement.
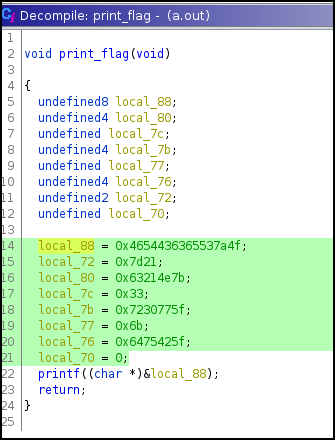
It appears to be in hex, so I copied and pasted each of those values into CyberChef.
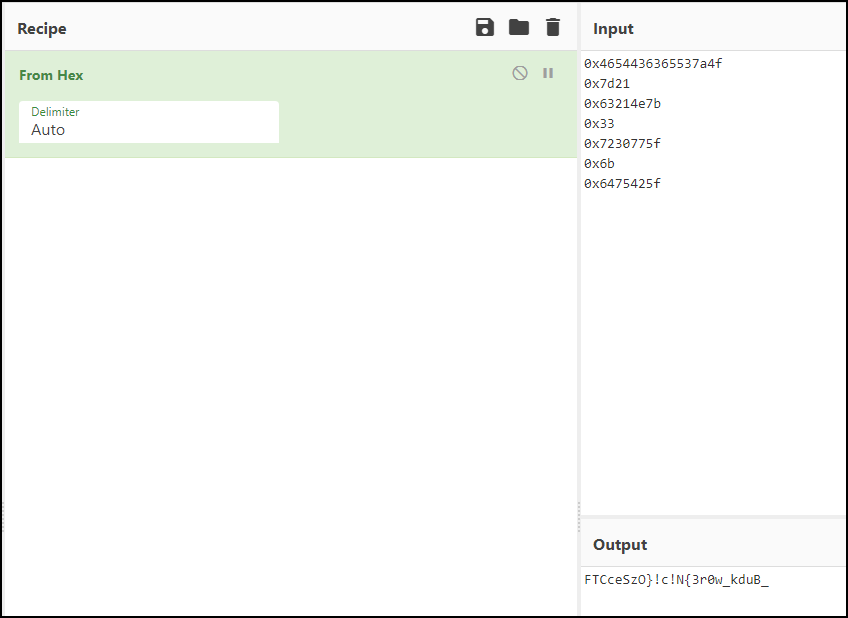
The flag looks reversed, so I reversed it. I then had to piece it back together.
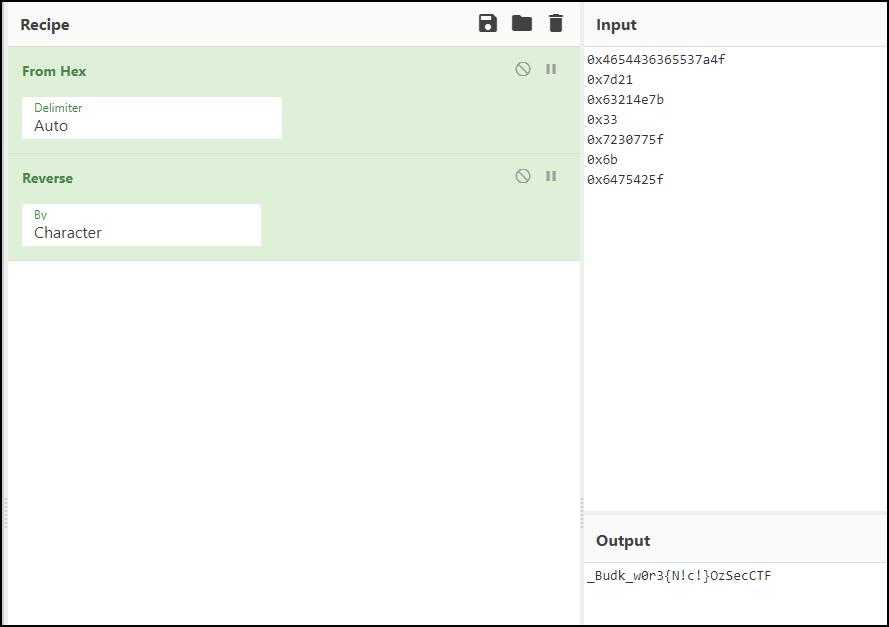
Final flag: OzSecCTF{N!c3_w0rk_Bud!}
- Points: 99
- Flag:
OzSecCTF{N!c3_w0rk_Bud!}
Classic web, PATCHED
Challenge Description
I can't have anything nice, you all just mess everything up. The only thing haccers after 2003 know is break code, web challenge XSS, eat taki's and lie.
I've made an updated site, you'll never be able to get secrets from this portal
https://classic-web-dot-breakict.uc.r.appspot.com/
Challenge Walkthrough
Loading the page and checking the Console we see a message saying the flag was loaded.
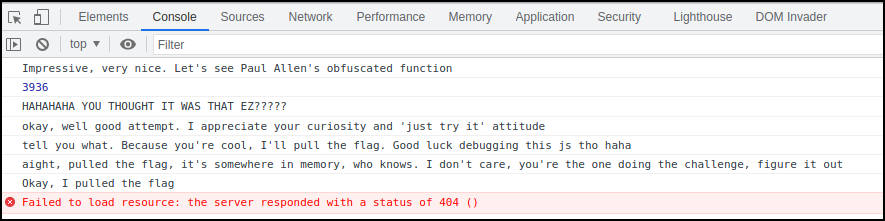
After manually running the get_flag() function:
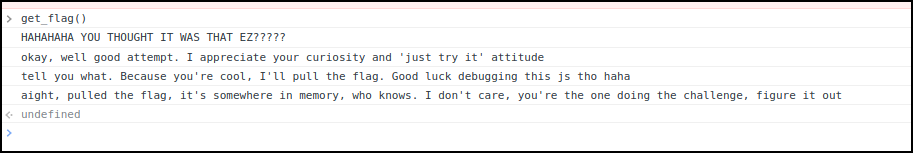
An XHR request appears:
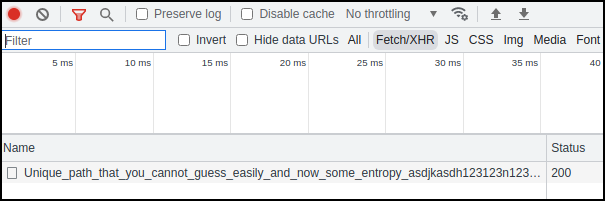
Loading that URL gets us the flag!
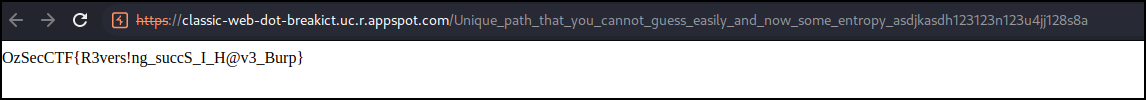
- Points: 200
- Flag:
OzSecCTF{R3vers!ng_succS_I_H@v3_Burp}